
半世人與失眠角力,落得身心渾沌,自知為愚癡所致,故曾竭力習禪除之。惟本人慧根拙劣,苦無習得幾分成果。禪修覺知之境,只得望洋興嘆。無奈續負無明之心,沉淪半夜虛妄幻想之中。故此,借化無明之心為創作,並取筆名「月無明」。
Sign SSL Certificate by Your Own CA with x509 extension
Following is introducing three layers SSL certificate chain
For adding x509 extension in certificate, a configuration files should be used rather than just type an option in command when you sign a certificate.
This topic introduces how to generate a SSL certificate chain with X509 extension.
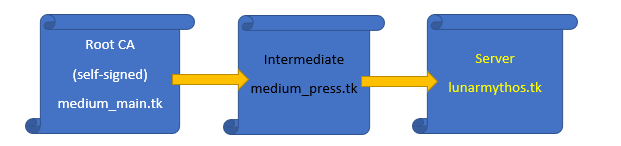
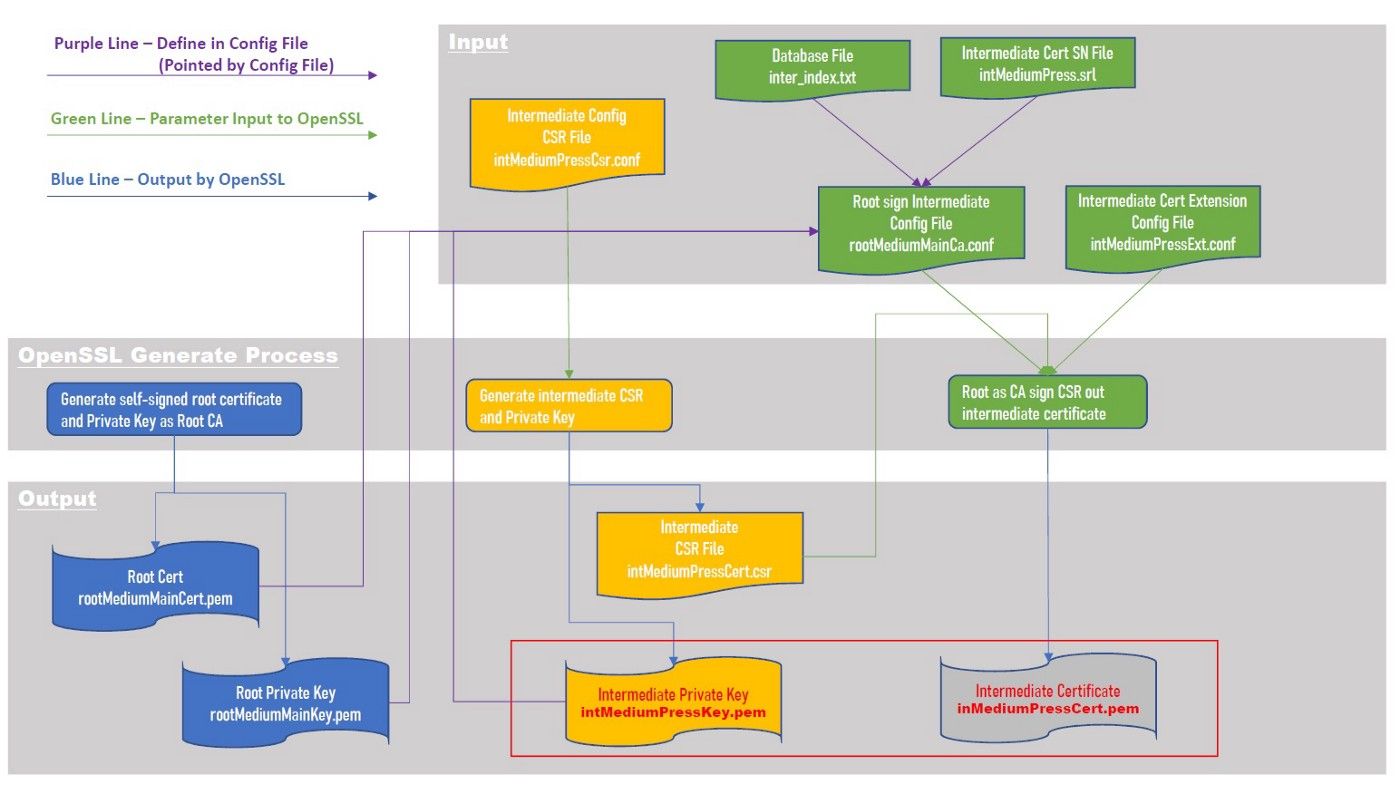
A. Root as CA Sign an Intermediate Certificate
A.1. Generate Self-sign Certificate to pretend a root CA and private key.
a. Command to generate self-signed CA root certificate and private key
=>rootMediumMainCert.pem, rootMediumMainKey.pem
# openssl req -x509 -days 3650 -newkey rsa:2048 -keyout rootMediumMainKey.pem -out rootMediumMainCert.pem
b. Check the certificate
# openssl x509 -in rootMediumMainCert.pem -text Certificate: Data: Version: 3 (0x2) Serial Number: d0:c1:93:56:ca:46:1f:d5 Signature Algorithm: sha256WithRSAEncryption Issuer: C=CN, ST=Hong KOng, L=Kwun Tong, O=MediumMain, OU=Publisher, CN=www.medium_main.tk Validity Not Before: Jul 25 09:54:55 2018 GMT Not After : Jul 22 09:54:55 2028 GMT Subject: C=CN, ST=Hong KOng, L=Kwun Tong, O=MediumMain, OU=Publisher, CN=www.medium_main.tk Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:d3:49:1f:42:5a:d7:7e:84:eb:2f:ae:79:2c:69: b2:2f:d2:b1:83:81:56:43:4d:ad:21:e7:a9:a7:ab: ce:d2:5a:a8:aa:ea:3d:d5:8d:7b:e1:9e:19:1a:32: f3:c9:31:00:fd:ac:f4:71:b4:38:7e:4c:5b:63:72: ca:9d:dd:4d:8d:65:b0:44:f8:00:1c:ad:84:25:f6: 30:aa:67:84:4e:cf:26:c4:98:5f:1f:1b:4c:64:a5: 4b:dc:a3:16:1d:f1:03:65:e8:e4:0a:33:61:fb:ed: da:24:75:c8:15:b7:55:d4:2c:3f:99:6f:3f:30:87: 84:33:c7:d3:2f:af:37:bd:88:ee:4c:35:6d:6b:2d: 6a:49:14:0d:ea:40:c4:07:eb:95:3b:e9:12:a7:3a: 19:b5:04:1b:1b:89:3f:ba:c7:9f:52:1a:36:78:55: 6f:85:94:c4:7d:e0:28:d2:41:27:6b:86:fe:c4:58: d2:66:6b:35:4b:f5:ef:a9:72:f6:c0:5c:fb:b1:98: 50:0b:da:42:60:75:08:5f:15:c5:56:38:23:64:49: 4c:8e:75:af:8c:2d:35:7f:fa:68:9e:cd:91:84:cd: 0b:3d:e7:53:71:64:26:b7:94:92:56:77:1e:79:dd: 04:a1:c5:8f:05:70:8d:bd:45:04:1d:03:18:a0:3d: ce:31 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Key Identifier: 07:8C:C1:29:24:98:D6:6B:0E:DA:05:3F:13:4E:30:FB:E0:39:EB:B0 X509v3 Authority Key Identifier: keyid:07:8C:C1:29:24:98:D6:6B:0E:DA:05:3F:13:4E:30:FB:E0:39:EB:B0 X509v3 Basic Constraints: CA:TRUE
2. Create Intermediate Certificate Request File
a. Prepare a configuration file for intermediate CSR file
=>intMediumPressCsr.conf
#This section is named req because the command we are using is req # (openssl req …) [ req ] # This specifies the default key size in bits. If not specified then 512 is # used. It is used if the -new option is used. It can be overridden by using # the -newkey option. default_bits = 2048 # This is the default filename to write a private key to. If not specified the # key is written to standard output. This can be overridden by the -keyout # option. default_keyfile = intMediumPressKey.pem # If this is set to no then if a private key is generated it is not encrypted. # This is equivalent to the -nodes command line option. For compatibility # encrypt_rsa_key is an equivalent option. encrypt_key = no # This option specifies the digest algorithm to use. Possible values include # md5 sha1 mdc2. If not present then MD5 is used. This option can be overridden # on the command line. default_md = sha256 # if set to the value no this disables prompting of certificate fields and just # takes values from the config file directly. It also changes the expected # format of the distinguished_name and attributes sections. prompt = no # if set to the value yes then field values to be interpreted as UTF8 strings, # by default they are interpreted as ASCII. This means that the field values, # whether prompted from a terminal or obtained from a configuration file, must # be valid UTF8 strings. utf8 = yes # This specifies the section containing the distinguished name fields to # prompt for when generating a certificate or certificate request. distinguished_name = my_req_distinguished_name # this specifies the configuration file section containing a list of extensions # to add to the certificate request. It can be overridden by the -reqexts # command line switch. See the x509v3_config(5) manual page for details of the # extension section format. req_extensions = my_extensions [my_req_distinguished_name] C = CN ST = Hong Kong L = Kwun Tong O = MediumPress OU = Press CN = www.medium_press.tk [my_extensions] basicConstraints=CA:TRUE extendedKeyUsage = serverAuth, clientAuth, codeSigning, emailProtection keyUsage = nonRepudiation, digitalSignature, keyEncipherment
b. Command to generate intermediate CSR file
=> intMediumPressCert.csr
# openssl req -new -out intMediumPressCert.csr -config intMediumPressCsr.conf
The private key file has been generated at the same time, this is based on the configuration parameter,
default_keyfile = intMediumPressKey.pem in configuration file.
3. Sign the intermediate certificate by root
a. Prepare extension configuration file for intermediate certificate
=>intMediumPressExt.conf
basicConstraints=CA:TRUE subjectKeyIdentifier = hash
b. Prepare ca configuration file for root CA certificate
=>rootMediumMainCa.conf
# ‘ca’ as the default section because we’re usign the ca command # we use ‘ca’ as the default section because we’re usign the ca command [ ca ] default_ca = ca_sign [ ca_sign ] # a text file containing the next serial number to use in hex. Mandatory. # This file must be present and contain a valid serial number. serial = ./intMediumPress.srl # the text database file to use. Mandatory. This file must be present though # initially it will be empty. database = ./inter_index.txt # specifies the directory where new certificates will be placed. Mandatory. new_certs_dir = ./intermediateCert # the file containing the CA certificate. Mandatory certificate = ./rootMediumMainCert.pem # the file contaning the CA private key. Mandatory private_key = ./rootMediumMainKey.pem # the message digest algorithm. Remember to not use MD5 default_md = sha256 # for how many days will the signed certificate be valid default_days = 1000 # a section with a set of variables corresponding to DN fields policy = my_policy [ my_policy ] # if the value is “match” then the field value must match the same field in the # CA certificate. If the value is “supplied” then it must be present. # Optional means it may be present. Any fields not mentioned are silently # deleted. countryName = match stateOrProvinceName = supplied organizationName = supplied commonName = supplied organizationalUnitName = optional commonName = supplied
c. Create a subdirectory (same as setting in rootMediumMainCa.conf) for placing output certificate temporary
# mkdir intermediateCert
d. Create text database file (same as setting in rootMediumMainCa.conf)
# touch inter_index.txt
e. Create serial number for output certificate by random number, the output serial number file is same as setting in rootMediumMainCa.conf
# echo $(od -vAn -N8 -tx8 < /dev/random) > intMediumPress.srl
f. Command to sign certificate
# openssl ca -config rootMediumMainCa.conf -out intMediumPressCert.pem -extfile intMediumPressExt.conf -in intMediumPressCert.csr
g. Check the certificate
# openssl x509 -in intMediumPressCert.pem -text Certificate: Data: Version: 3 (0x2) Serial Number: 8407366217844970047 (0x74acf707ef44d23f) Signature Algorithm: sha256WithRSAEncryption Issuer: C=CN, ST=Hong KOng, L=Kwun Tong, O=MediumMain, OU=Publisher, CN=www.medium_main.tk Validity Not Before: Jul 26 02:43:40 2018 GMT Not After : Apr 21 02:43:40 2021 GMT Subject: C=CN, ST=Hong Kong, O=MediumPress, OU=Press, CN=www.medium_press.tk Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:df:77:59:11:d3:b6:da:01:1f:64:69:18:18:a0: ba:11:da:b3:ef:55:4e:7c:4c:92:43:b7:73:20:83: 9c:34:86:ed:ce:df:b8:a5:09:7e:88:51:68:08:21: b9:e6:e6:1e:33:99:07:bb:9f:be:96:24:7c:1c:27: 92:3f:16:c5:e8:a8:46:26:56:4f:2e:ac:a5:69:48: cd:37:03:d2:4d:87:75:ce:53:34:94:86:f6:cd:8b: a5:f7:0f:c2:ec:70:b3:d7:78:5d:2f:21:de:61:87: 72:8e:c5:57:ad:be:f6:92:93:ec:db:77:1a:30:6f: 4b:9b:77:7b:0f:98:77:05:3f:7a:da:7b:e1:59:57: 54:65:65:68:26:86:7d:22:90:91:e4:b1:4a:b1:c0: c9:ce:c6:45:e0:96:94:46:6d:c4:3f:84:ae:85:e0: 4a:42:ac:c3:83:7d:da:c5:b3:a7:a4:c0:e6:6e:45: 8d:55:b8:4c:b4:11:01:01:cc:a5:5b:92:d7:a2:16: 3e:61:d9:38:f0:46:5b:9d:2e:d2:ad:a9:cc:57:e3: 2e:8f:92:c4:15:65:53:35:46:d2:8b:3f:ef:8f:55: 87:ac:ed:ea:e2:a5:5d:c9:9b:e8:f9:14:a6:7a:72: 06:57:14:11:ce:36:3b:8d:59:20:d7:9f:b0:0d:24: 91:19 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Basic Constraints: CA:TRUE X509v3 Subject Key Identifier: 9B:9F:CC:D0:E8:53:B0:45:CA:4A:D8:44:56:62:80:B2:F7:22:AD:B8
B. Intermediate Certificate Sign a Server
We have already done a intermediate certificate signed by own CA root certificate, now let cascade the procedure to sign a certificate chain to produce server certificate eventually.
1. Create Server Certificate Request File
a. Prepare a configuration file for server CSR file
=>serverLunarMythosCsr.conf
#This section is named req because the command we are using is req # (openssl req …) [ req ] # This specifies the default key size in bits. If not specified then 512 is # used. It is used if the -new option is used. It can be overridden by using # the -newkey option. default_bits = 2048 # This is the default filename to write a private key to. If not specified the # key is written to standard output. This can be overridden by the -keyout # option. default_keyfile = serverLunarMythosKey.pem # If this is set to no then if a private key is generated it is not encrypted. # This is equivalent to the -nodes command line option. For compatibility # encrypt_rsa_key is an equivalent option. encrypt_key = yes # This option specifies the digest algorithm to use. Possible values include # md5 sha1 mdc2. If not present then MD5 is used. This option can be overridden # on the command line. default_md = sha256 # if set to the value no this disables prompting of certificate fields and just # takes values from the config file directly. It also changes the expected # format of the distinguished_name and attributes sections. prompt = no # if set to the value yes then field values to be interpreted as UTF8 strings, # by default they are interpreted as ASCII. This means that the field values, # whether prompted from a terminal or obtained from a configuration file, must # be valid UTF8 strings. utf8 = yes # This specifies the section containing the distinguished name fields to # prompt for when generating a certificate or certificate request. distinguished_name = my_req_distinguished_name # this specifies the configuration file section containing a list of extensions # to add to the certificate request. It can be overridden by the -reqexts # command line switch. See the x509v3_config(5) manual page for details of the # extension section format. req_extensions = my_extensions [my_req_distinguished_name] C = CN ST = Hong Kong L = Kwun Tong O = Lunar Mythos OU = Press CN = www.lunarmythos.tk [my_extensions] basicConstraints=CA:TRUE extendedKeyUsage = serverAuth, clientAuth, codeSigning, emailProtection keyUsage = nonRepudiation, digitalSignature, keyEncipherment
b. Generate Server Certificate Sign Request File based on configuration file in step a.
=>serverLunarMythosCert.csr
# openssl req -new -out serverLunarMythosCert.csr -config serverLunarMythosCsr.conf
2. Sign a server certificate by intermediate
a. Prepare extension configuration file for server certificate
=>serverLunarMythosExt.conf
basicConstraints=CA:TRUE subjectKeyIdentifier = hash
b. Prepare CA configuration file for intermediate certificate as CA
=>intMediumPressCa.conf
#’ca’ as the default section because we’re usign the ca command # we use ‘ca’ as the default section because we’re usign the ca command [ ca ] default_ca = ca_sign [ ca_sign ] # a text file containing the next serial number to use in hex. Mandatory. # This file must be present and contain a valid serial number. serial = ./serverLunarMythos.srl # the text database file to use. Mandatory. This file must be present though # initially it will be empty. database = ./server_index.txt # specifies the directory where new certificates will be placed. Mandatory. new_certs_dir = ./serverCert # the file containing the CA certificate. Mandatory certificate = ./intMediumPressCert.pem # the file contaning the CA private key. Mandatory private_key = ./ intMediumPressKey.pem # the message digest algorithm. Remember to not use MD5 default_md = sha256 # for how many days will the signed certificate be valid default_days = 365 # a section with a set of variables corresponding to DN fields policy = my_policy [ my_policy ] # if the value is “match” then the field value must match the same field in the # CA certificate. If the value is “supplied” then it must be present. # Optional means it may be present. Any fields not mentioned are silently # deleted. countryName = match stateOrProvinceName = supplied organizationName = supplied commonName = supplied organizationalUnitName = optional commonName = supplied
b. Create a subdirectory (consistent to setting in rootMediumMainCa.conf) for placing output server certificate temporary.
# mkdir serverCert
b. Create text database file (consistent to setting in rootMediumMainCa.conf)
# touch server_index.txt
c. Create serial number file for output certificate by random number. (File name should be consistent to setting in rootMediumMainCa.conf
# echo $(od -vAn -N8 -tx8 < /dev/random) > serverLunaryMythos.srl
d. Command to sign certificate
# openssl ca -config intMediumPressCa.conf -out serverLunarMythosCert.pem -extfile serverLunarMythosExt.conf -in serverLunarMythosCert.csr
e. Check the final server certificate
# openssl x509 -in serverLunarMythosCert.pem -text Certificate: Data: Version: 3 (0x2) Serial Number: f0:d6:cb:dd:46:37:fb:c0 Signature Algorithm: sha256WithRSAEncryption Issuer: C=CN, ST=Hong Kong, O=MediumPress, OU=Press, CN=www.medium_press.tk Validity Not Before: Jul 26 03:32:12 2018 GMT Not After : Jul 26 03:32:12 2019 GMT Subject: C=CN, ST=Hong Kong, O=Lunar Mythos, OU=Press, CN=www.lunarmythos.tk Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:ad:1d:0e:b3:76:1e:57:eb:fc:60:b8:3c:d0:0d: aa:25:e9:b0:01:d8:8d:c3:2a:45:04:1d:8c:38:fc: 10:c4:b8:96:95:6b:6f:0e:73:72:8d:04:38:72:72: 7f:fe:9a:78:4b:30:86:96:81:00:5a:ef:75:b8:e8: bd:04:92:cd:c0:92:69:33:45:26:b3:9f:48:a7:4b: 02:09:a8:cd:57:a7:b8:e1:2b:a2:01:28:ec:dd:6b: e3:17:5e:f8:e9:31:b5:48:46:a0:6c:7c:f6:f8:fe: ac:b5:04:c1:9b:d1:d9:56:9d:3d:10:be:41:3a:9a: 5b:11:8a:a5:3a:4c:31:5c:d5:ca:7e:2c:28:c1:b3: bf:5b:28:97:59:a3:5b:c4:05:24:d7:93:16:74:7a: 1d:e6:4e:f8:e9:af:54:0f:d8:8f:2d:60:07:d6:4c: 70:b4:38:73:3e:16:7c:d3:cb:29:c4:81:bd:c5:cb: ff:4e:b5:2e:a3:bb:7d:a8:39:bc:47:cd:4c:58:74: 3c:cc:a9:2a:43:5a:0f:09:e2:e3:35:a1:23:63:90: 85:57:82:d2:d5:07:d9:ee:41:80:db:94:8c:37:f5: e2:b2:4b:ae:c9:4f:d6:c7:b9:14:1b:f1:0f:b2:6c: 7d:ae:c9:21:e9:a2:3a:f4:cd:91:db:85:5d:4b:a7: 08:af Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Basic Constraints: CA:TRUE X509v3 Subject Key Identifier: B9:C8:8D:41:D1:03:83:3A:38:BE:0F:30:08:60:45:AE:88:BE:06:01
C. Final Verification of Certificate Chain
openssl verify -CAfile rootMediumMainCert.pem -untrusted intMediumPressCert.pem serverLunarMythosCert.pem serverLunarMythosCert.pem: OK
— END —
喜欢我的文章吗?
别忘了给点支持与赞赏,让我知道创作的路上有你陪伴。
发布评论…